Someone is Controlling My Computer Remotely – What to Do?
Have you ever felt like someone else has access to your computer? If you suspect that someone is controlling your computer remotely, don’t panic. In this article, we’ll discuss what you can do to take control back.
Signs that someone is remotely controlling your computer
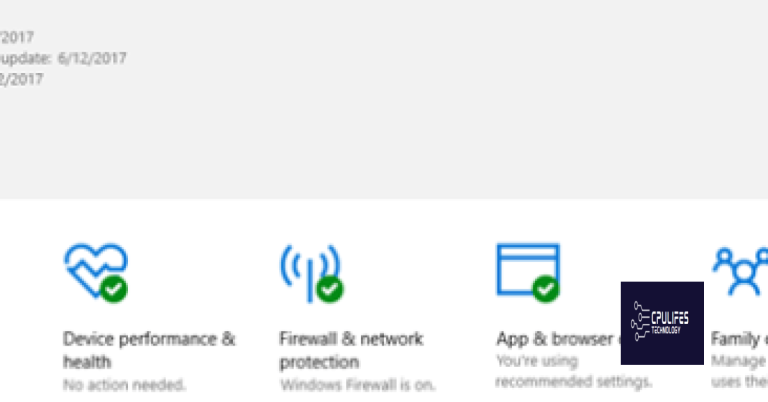
If you suspect someone is remotely controlling your computer, there are a few signs you can look for. Your mouse may move on its own, programs may open or close without your permission, and files may be added or deleted. Additionally, your computer may run slower than usual, or you may notice strange pop-ups or messages. If you suspect someone is remotely controlling your computer, disconnect your internet connection immediately to prevent further access. Then, run a full virus scan to identify any malware or spyware on your device. Consider changing your passwords, and if you have remote support software installed like TeamViewer, remove it from your device. Contact a professional if you are unsure how to proceed.
It can also automatically fix any missing or corrupt DLL files. In severe cases like the Blue Screen of Death, Fortect can repair the causes such as incompatible DLLs, drivers, and Windows bugs, and even identify malfunctioning hardware that may need replacement. Moreover, if you need to recover your operating system, Fortect can compare it with a healthy version and restore any vital system files without affecting your data.
How to check if someone is accessing your computer without permission
- Check for signs of remote access
- Look for unexplained mouse movements, clicks, or commands
- Check your open applications and see if any are running that you did not start
- Look for unusual pop-ups or error messages
- Check your computer’s network activity to see if data is being sent or received without your knowledge
- Run a malware scan
- Use a reputable anti-virus or anti-malware software to scan your computer for any malicious software or viruses
- If any are found, follow the program’s instructions to remove them
- Check your remote access settings
- Go to your computer’s control panel and open the system and security settings
- Click on the system icon and then go to remote settings
- Make sure that remote access is turned off or set to only allow connections from trusted sources
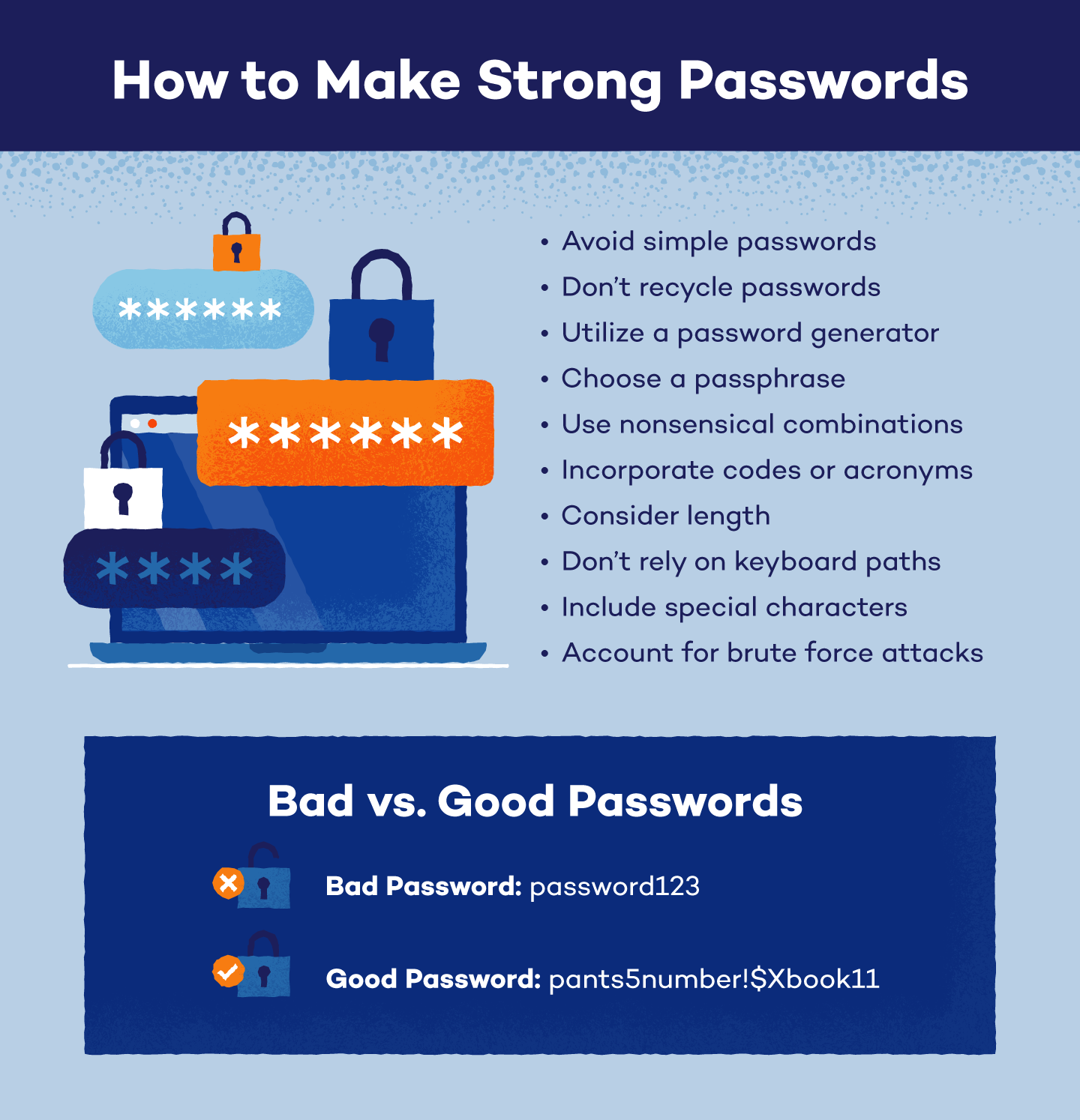
- Change your passwords
- Change your computer’s login password and any other passwords associated with your accounts
- Make sure to use strong, unique passwords that are difficult to guess or crack
- Enable two-factor authentication
- Set up two-factor authentication on any accounts that offer it, such as email or social media accounts
- This will add an extra layer of security to your accounts and make it more difficult for someone to access them without your permission

- Consider contacting a professional
- If you are still unsure if someone is accessing your computer without permission, consider contacting a computer security professional for help
- They can help you identify any security weaknesses and provide guidance on how to better protect your computer and personal information

Steps to take if you suspect someone is controlling your computer
If you suspect that someone is controlling your computer remotely, there are a few steps you can take to protect yourself. First, disconnect your computer from the internet to prevent any further access. Then, run a virus scan to identify and remove any malware that may have allowed the remote access. If you have any remote support software installed, such as TeamViewer, uninstall it immediately. Change your passwords for all accounts, especially if you use the same password for multiple accounts. If you have an iPhone, iPad, or Mac, enable two-factor authentication for added security. If you suspect that a hacker was behind the remote access, report it to the authorities and consider contacting a cybersecurity expert. Taking these steps will help protect your personal information and prevent further unauthorized access to your devices.
import keyboard
def detect_control():
control_keys = ['ctrl', 'alt', 'shift', 'win']
while True:
keys_pressed = keyboard.get_pressed()
for key in control_keys:
if keys_pressed[keyboard.keycodes[key]]:
print(f'{key} key pressed - possible control detected!')
# add code here to prevent/control the control
This code uses the `keyboard` library to detect when certain control keys (e.g. ctrl, alt, shift, win) are pressed. If any of these keys are detected, the code will print a message indicating that a possible control has been detected. From here, additional code could be added to prevent or control the detected control.
It is important to note that this code is only a starting point and additional work would be needed to create a fully functional tool to detect and prevent someone from controlling a computer.
Preventing unauthorized access to your computer and data
| Preventing Unauthorized Access to Your Computer and Data | |
|---|---|
| 1. | Use strong passwords and change them often. |
| 2. | Install and regularly update anti-virus and anti-malware software. |
| 3. | Keep your operating system and software up to date with the latest security patches. |
| 4. | Enable your computer’s built-in firewall or install a third-party firewall. |
| 5. | Be cautious when opening email attachments or clicking on links from unknown senders. |
| 6. | Use two-factor authentication whenever possible. |
| 7. | Encrypt sensitive data and secure it with strong passwords. |
Beware, it seems like someone is gaining unauthorized control over my computer. Download this tool to run a scan